With reading for tomorrow on honeynets and next Tueday on Stuxnet.
Archive for the ‘Uncategorized’ Category
Course schedule is updated
Wednesday, April 6th, 2011Group 2 – CVE-2006-0105
Wednesday, April 6th, 2011Group 1 CVE-2009-4484
Monday, April 4th, 2011XSS on a Page Rank 5 Site
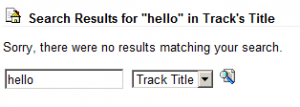
Sunday, April 3rd, 2011So I was visiting a website that I frequent pretty often to download recordings (non-copyright, legal fyi) and check the latest posts on the forum (link not included for security). Then recently, I searched for a recording and noticed that the search entry was displayed on the page:
Well, are you thinking what I’m thinking?
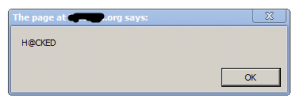
I decided to enter a :
<script> alert(“H@CKED”) </script>
and sure enough
This page rank 5 website was indeed vulnerable to cross site scripting.
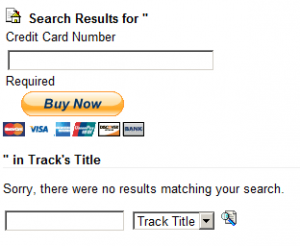
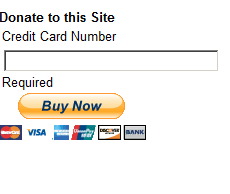
To test what inputs could be put in I decided to see if standard html would display correctly, perhaps a paypal buy now button?
And to get rid of the ” in Track’s Title…”, one could just put in a <!– to comment it out:
What’s even worse is that the search entry is made via a GET in the URL.
Now this is a big problem. An attacker just needs to craft a URL and get some one to click on to potentially:
- Convince them that they can donate to the website, when they are really donating to the attacker
- Steal account login via javascript, which is a particular problem given that the forum has over 8000 users
The best way to deal with this problem would be to sanitize inputs or display them as text, escaping from the html
In order to deal with this ethically, the administrator of the website will be contacted and informed. A public
announcement will be made 30 days after informing the administrator if no change is made.
Group 5 CVE-2009-0696
Sunday, April 3rd, 2011Group 3 CVE-2010-4015
Wednesday, March 30th, 2011Fortify Educational License Agreement
Thursday, March 17th, 2011In case anybody wants to read the legalese, I’m attaching the contract that you’ll be agreeing to abide by for our next project. Fortify Educational License Agreement_360
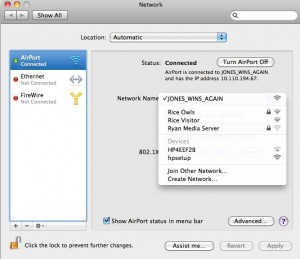
JONES_WINS_AGAIN?
Friday, March 11th, 2011
In the past week, you might have noticed a new Wireless network available around Rice campus: JONES_WINS_AGAIN (a favorite cheer of my college, Jones).
This wireless network was created as part of a jack for Willy Week. When I first saw it, I wasn’t sure what had happened – my first thought was that members of another college had created a local wireless network at Jones College in an effort to gain user data and credentials of Jones students who would foolishly connect to a wireless network named in their honor. This would be highly unethical, and so of course this wasn’t the case. Rather, the JONES_WINS_AGAIN wireless network was being broadcast from every Rice Access Point on campus and acted identical to the Rice Visitor network.
So how did we do it? Did a member of Jones manage to hack into Rice Wireless? Sorta. Thanks to the Associate Program at Rice, Rice’s Senior Network Architect Danny Eaton is proudly associated with Jones College, and he was able to execute this “attack” because of his admin status. He created a new network, gave it a SSID of “JONES_WINS_AGAIN” and gave it all the same security settings as the Rice Visitor network. Once set up, the Access Points around campus would broadcast it.
This doesn’t mean people will use it though. Most computers have already been configured to automatically connect to Rice Owls or Rice Visitor, so you’d have to know to connect to this new network. Additionally, I’m sure some people had the same initial thought as I about the mysterious network – that it was somehow malicious. In talking with Danny Eaton, I learned some usage statistics of the network. As I’m writing this, ~35 people are connected to the JONES_WINS_AGAIN (as compared to the ~3500 users currently connected to Rice Owls). It has been active for the past week, and at the network’s peak, it had 55 users connected. So it didn’t exactly make much of an impact, but it is an interesting (and simple) attack none the less.
WinAmp Security
Tuesday, March 1st, 2011A few months back, I registered on the WinAmp forums because I was experiencing some bugs with the music player. Just a few days ago, I found the following email in my inbox:
“Hello,
My name is Geno Yoham and I am the General Manager of Winamp. First, thank you for your support of Winamp. The Winamp Team is dedicated to providing you with the best possible media player experience so it gives us great pain to notify you that we have recently experienced a security breach of our user forums database.
We have confirmed that your email address was exposed as a result of this attack. We have not confirmed but must assume that other Winamp Forums user account detail, including your forums username, date of birth, time zone preference and encrypted paWinssword (not your clear text or unencrypted password) was exposed. The Winamp Forums are now secure, but because we value your privacy we would like to notify you of the incident and encourage you to immediately change your password as a precautionary measure. If you have used your Winamp forums password across other web sites, please change the password on those web sites as well.
We apologize for any inconvenience this has caused and want to assure you that we are taking steps to ensure that your information remains secure as a part of our ongoing commitment to protecting your privacy.
If you have any questions, please contact: support@winamp.com. We have also set up an FAQ atforums.winamp.com for answers to common questions you may have related to this incident.
Geno Yoham
Winamp”
Well, great. I remember registering on the forums with the same password I use for a good number of other sites on the net and I used my primary email address for the forums – and I’m sure many others did the same. Now a hacker has a full list of emails and associated encrypted passwords. By simply hashing generated passwords and seeing if they match any user’s encrypted password, the attacker could identify passwords, linked to emails, as well as the date of birth, and can gain access to many different email accounts and who knows what else. Discovering passwords is a lot easier when you have a list of thousands of potential accounts to crack, and I’m sure many used the same password to log-in to their email account. And if even they use a different password for their email, many sites, like facebook, use an email address as the username to log-in, which can lead to even more problems.
I guess this is just a reminder of how insecure the internet is and how vulnerable your information is online. Although it would be best to use different passwords for every registration on the internet, it may be too cumbersome. Fortunately there are a good number of programs that take can care of the problem for you. A great (and free) tool is roboform (http://www.roboform.com/), which acts as a secure password manager. It automatically generates strong passwords when you register for a website and remembers them so you don’t have to. It even securely backs up your passwords and can sync with your phone, other browsers, etc. As for your email, it would be good to have a dedicated spam email address or you can use temporary email accounts like mailinator.
HW3 due date update
Sunday, February 20th, 2011It’s due Thursday night. The schedule was right. The homework page itself was mistaken. Sorry for any confusion.