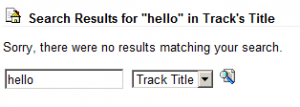
So I was visiting a website that I frequent pretty often to download recordings (non-copyright, legal fyi) and check the latest posts on the forum (link not included for security). Then recently, I searched for a recording and noticed that the search entry was displayed on the page:
Well, are you thinking what I’m thinking?
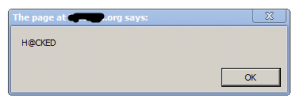
I decided to enter a :
<script> alert(“H@CKED”) </script>
and sure enough
This page rank 5 website was indeed vulnerable to cross site scripting.
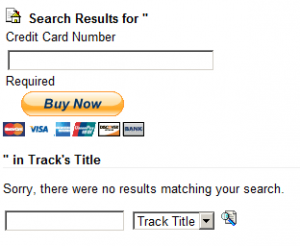
To test what inputs could be put in I decided to see if standard html would display correctly, perhaps a paypal buy now button?
And to get rid of the ” in Track’s Title…”, one could just put in a <!– to comment it out:
What’s even worse is that the search entry is made via a GET in the URL.
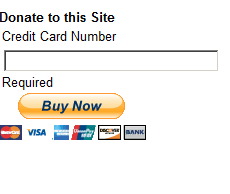
Now this is a big problem. An attacker just needs to craft a URL and get some one to click on to potentially:
- Convince them that they can donate to the website, when they are really donating to the attacker
- Steal account login via javascript, which is a particular problem given that the forum has over 8000 users
The best way to deal with this problem would be to sanitize inputs or display them as text, escaping from the html
In order to deal with this ethically, the administrator of the website will be contacted and informed. A public
announcement will be made 30 days after informing the administrator if no change is made.


If there’s a login at all, you can also use that trick to steal cookies.